CASB Deployment
By David Xiao
TL;DR
Cloud Access Security Broker (CASB) is considered a common solution to mitigate shadow IT and data exfiltration risks on many organization’s migrating to cloud journey.
This post discussed some common deployment architecture and use cases respectively.
CASB and Context Aware Access
CASB can mitigate data exfiltration risks from insider - it can correlate the download of sensitive data from a managed cloud service with the upload of that data to a personal cloud service.
Context Aware Access is focusing on mitigating authentication and authorization risks and promoting a “Zero Trust” access model in VPN-less settings.
Reverse proxy
A reverse proxy deployment steers browser-based cloud traffic from managed cloud apps to the CASB Cloud.
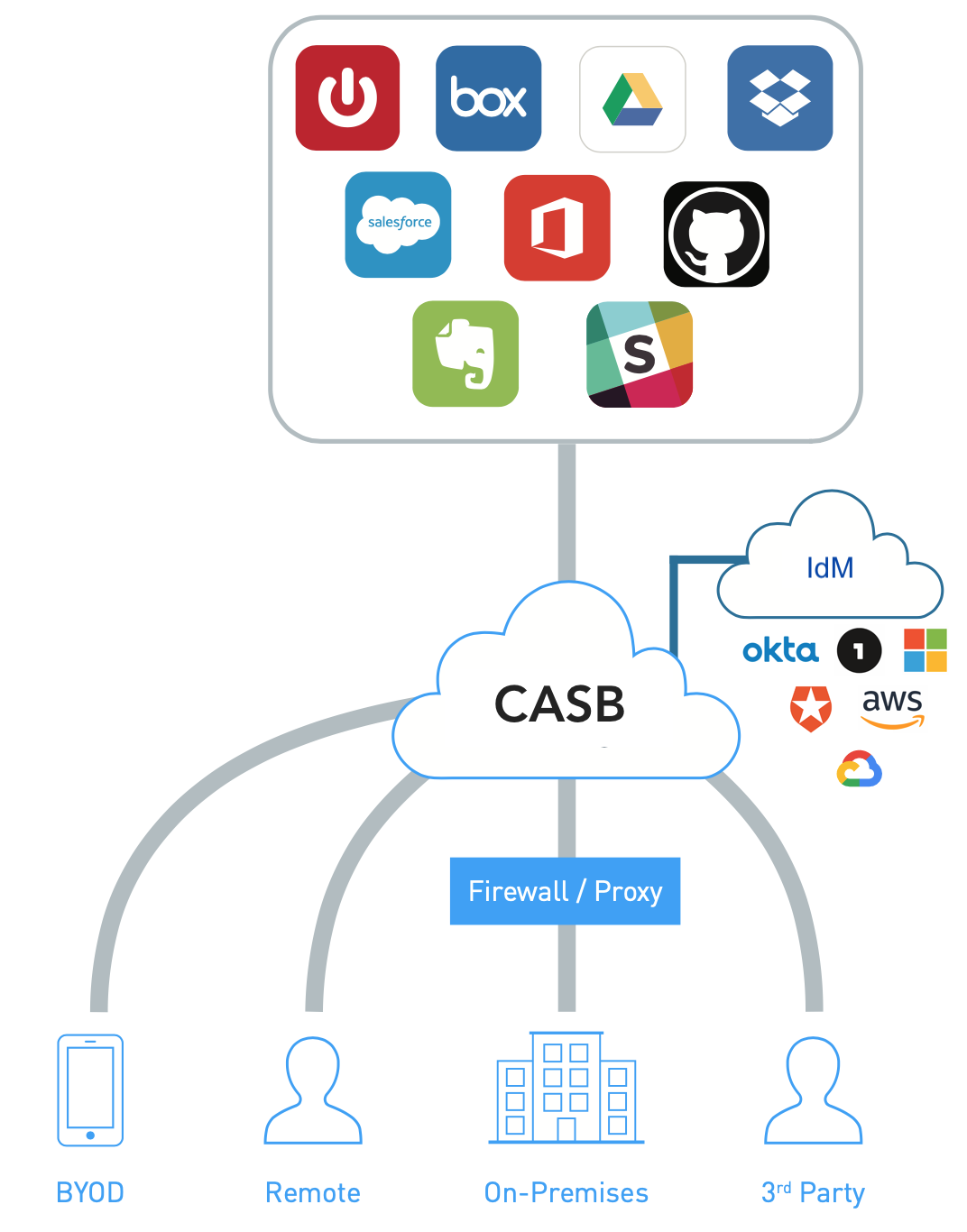
Reverse Proxy Deployment
A CASB in reverse proxy mode proxies all traffic to and from cloud apps. Unlike a forward proxy, the endpoint or network does not need to be managed.
A common approach is to leverage the organization’s identity solution (IdM), for example Okta, to route traffic through the CASB reverse proxy following authentication. In this way, all traffic bound for a cloud service is pervasively steered over to the CASB proxy.
Reverse proxy is essentially the only deployment architecture that supports both managed and unmanaged devices accessing cloud apps.
Challenges
It supports web browser traffic only – native apps or sync clients may have non-web authentication methods. (e.g. JWT or other forms of API token)
Forward proxy
CASB forwarder is deployed on-premises as a VM that steers local cloud and web traffic to the CASB Cloud.
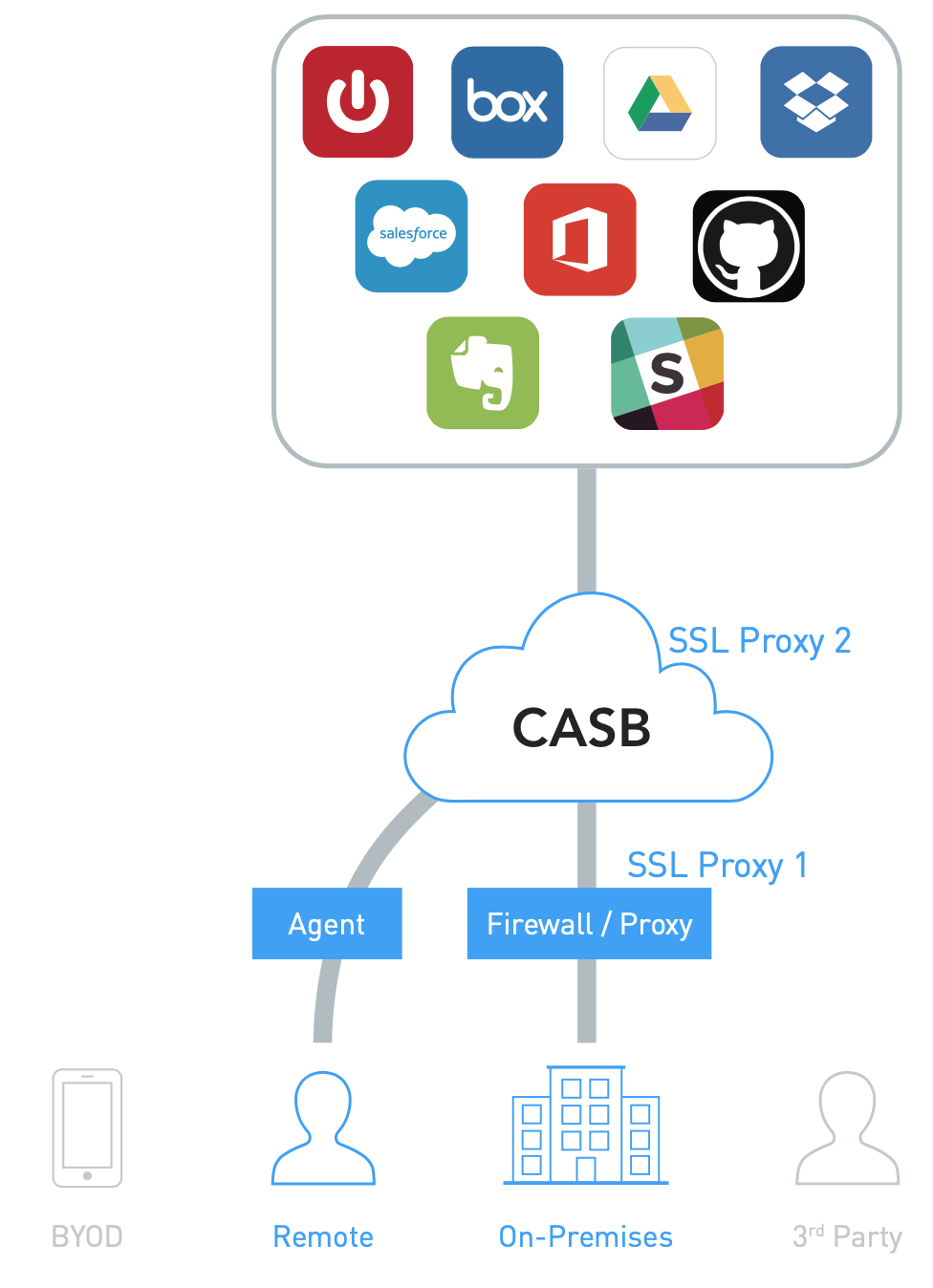
Forward Proxy Deployment
There are two approaches:
If the organization has an existing secure web gateway, a common practice is to configure proxy chaining to the upstream CASB forward proxy.
If no secure web gateway exists, an endpoint agent can be deployed to route cloud traffic through the forward proxy.
Challenges
It does not work well for either unmanaged devices or users that are accessing cloud over non-corporate network, e.g. at home.
API
Use API connectors to connect CASB to cloud apps like Office 365, Box, Salesforce that offer APIs to support visibility and policy enforcement.
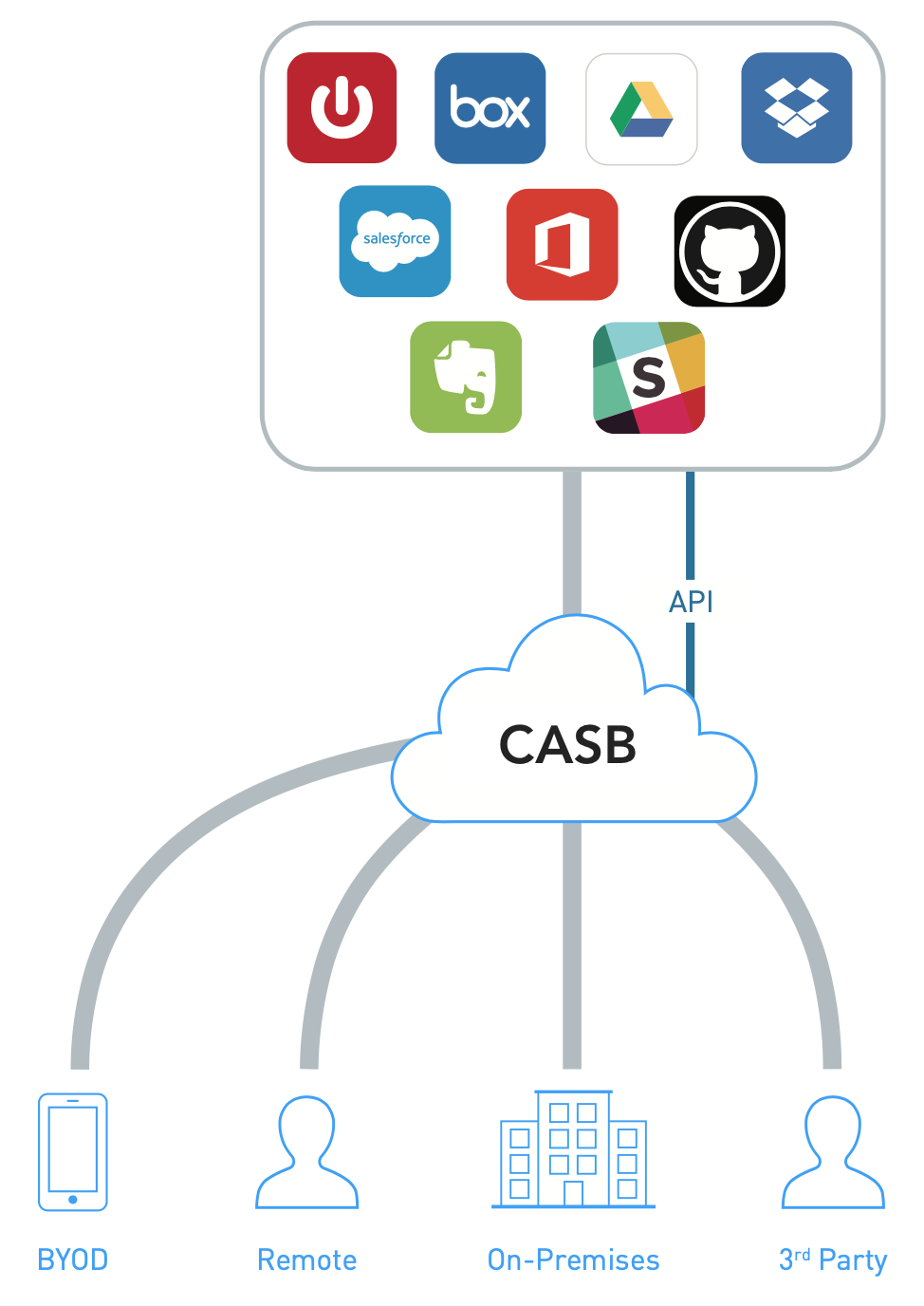
API Deployment Architecture
Typical APIs such as audit trails of user activity, content inspection, user permissions on storage and security settings can be leveraged by CASB to enable visibility and policy enforcement.
Challenges
-
Does not discover “Shadow IT”.
-
CASB vendor may not support Cloud apps that end user currently uses or choose to use in the future.
-
API based capabilities vary for each Cloud app.
Log collection
CASB can be configured to parse log traffic from a perimeter device. This provides cloud service discovery capabilities. Logs can be uploaded directly to the CASB Cloud or an on-premises log parser can be deployed to continuously send log data to the CASB.
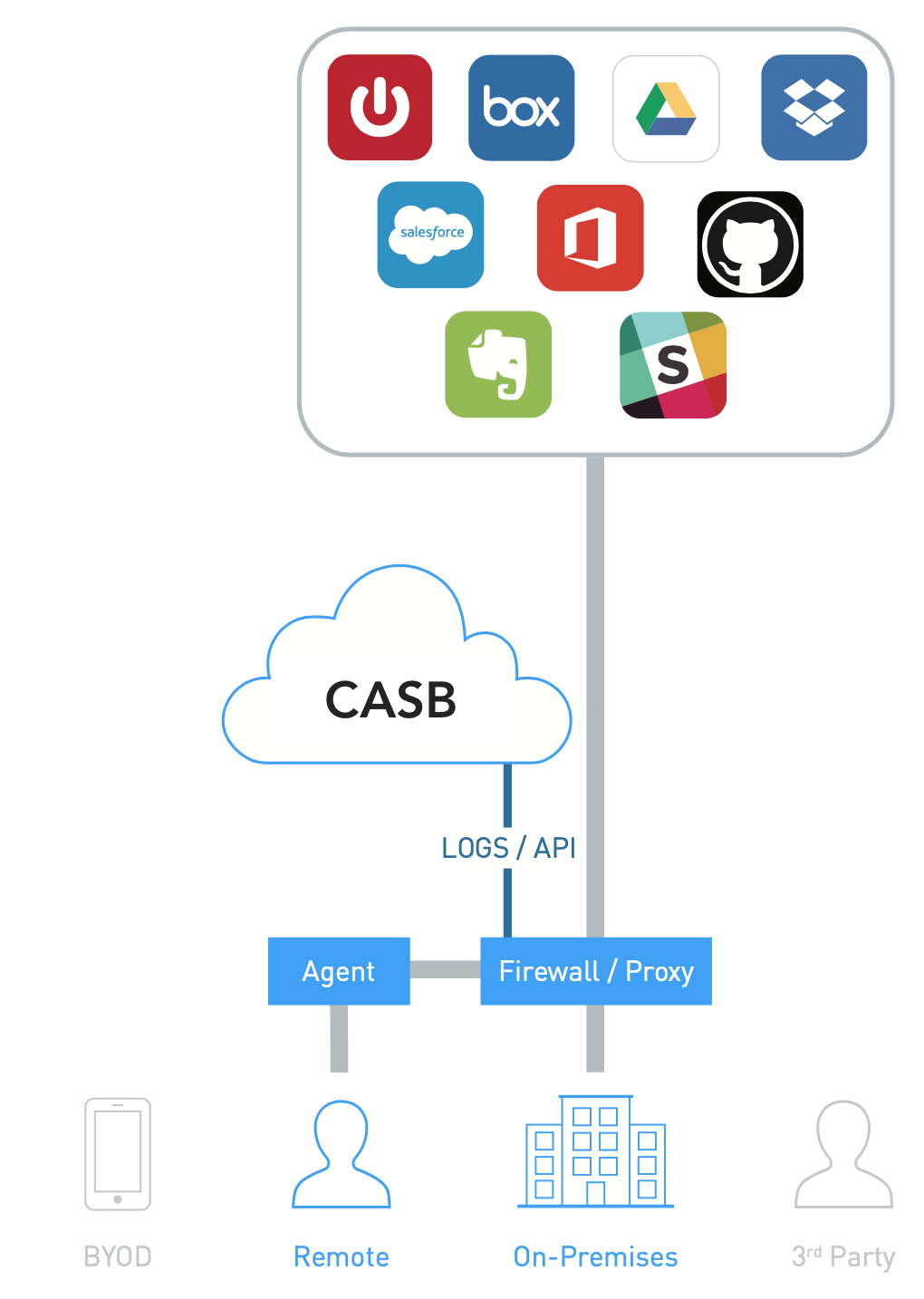
Log Collection Deployment
Challenges
Logs may not be support off-the-shelf, customization may be required.
Reference
CASB Deployment Options (Netskope)