Threat Modeling and STRIDE Model
By David Xiao
TLDR: This post is my collection of articles related to threat modeling and Microsoft STRIDE threat model.
What Is Threat Modeling
At a high level, threat modeling is a process of putting the “bad guy” hat on and conducting an security assessment over a system (such as a website or a mobile app) to identify and prioritize threats and mitigations.
A more complete definition can be found on Wikipedia.
There are many ways to do threat modeling. Depending on the types of system and workloads that are in scope, the applicable threats can vary a lot.
For example, threat modeling over a set of highly scalable workloads deployed on MS Azure might start from a threat library that includes portential threats relevant to Azure services in use, while assessing over a simple web application hosted on on-prem data center might start from a different set of threats relevant to host based security and OWASP Top 10.
What Is STRIDE
STRIDE is both a threat model framework and a methodology that developed and adopted in Microsoft over the years.
STRIDE stands for:
-
Spoofing: Impersonating something or someone else.
-
Tampering: Modifying data or code.
-
Repudiation: Claiming to have not performed an action.
-
Information Disclosure: Exposing information to someone not authorized to see it.
-
Denial of Service: Deny or degrade service to users.
-
Elevation of Privilege: Gain capabilities without proper authorization.
Microsoft suggests the following approach when conducting a threat modeling:
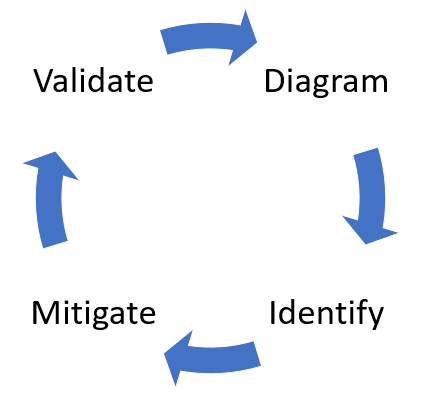
Threat Modeling Process
Most Current Articles
Threat Modeling. A high level overview.
Azure Threat Modeling Tool, the framework and the tool. 02/16/2017
Older References
STRIDE chart 09/11/2007
Threat Modeling, once again 08/30/2007
Threat Modeling again. Drawing the diagram 08/31/2007
Threat Modeling Again, STRIDE 09/04/2007
Threat Modeling Again, STRIDE Mitigations 09/05/2007
Threat Modeling Again, What does STRIDE have to do with threat modeling 09/07/2007
Threat Modeling Again, STRIDE per Element 09/10/2007
Threat Modeling Again, Threat Modeling PlaySound 09/11/2007